FreeBSD Remote Serial Console Access With Dell and Cisco Servers
Mon 01 May 2017 by feldI have become allergic to Java. It seems every time I need to access a server console my system is throwing fits about Java security. I've spent hours trying to fix a Java issue which was preventing me from fixing a server I needed console access to. I will show you how to end this madness.
FreeBSD
You should always enable the serial console on your servers. You never know when you will need it, and it is a prerequisite for this exercise. On FreeBSD you will want to do the following:
/boot/loader.conf:
boot_multicons="YES"
boot_serial="YES"
comconsole_speed="115200"
console="comconsole,vidconsole"
Enable ttyu0 always by changing onifconsole to on in /etc/ttys:
ttyu0 "/usr/libexec/getty 3wire" vt100 on secure
On releases before 10.3-RELEASE you also change std.9600 to std.115200 as 3wire is not available:
ttyu0 "/usr/libexec/getty std.115200" vt100 on secure
When complete you will need to enable it with kill -HUP 1. You can find more details on this in the FreeBSD handbook.
Dell DRAC
On Dell servers you will need to enable the serial console in the BIOS. If you have multiple serial ports the following configuration should allow both the physical and virtual serial ports to function as intended. Here is a screenshot of my BIOS settings:
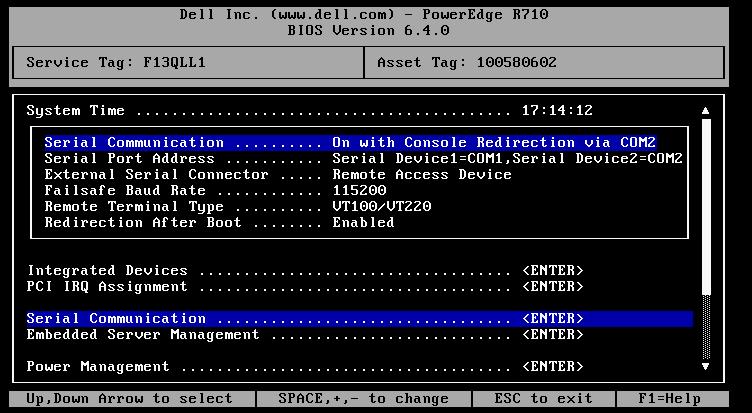
You will also want to enable IPMI. This can be done in the DRAC settings on boot in the following screenshot, or you can SSH to the DRAC console and enable it there with the rest of the settings.
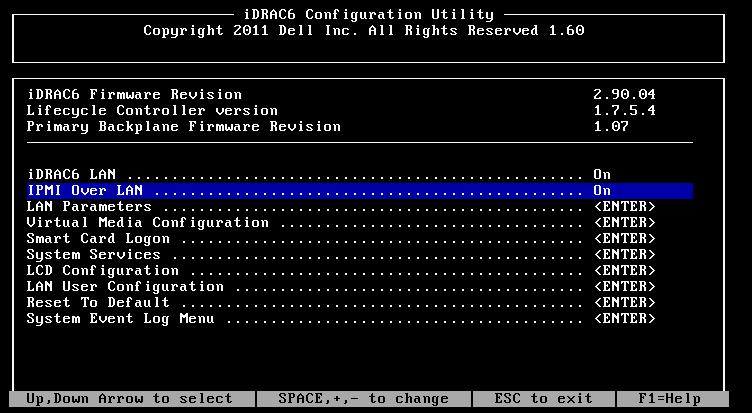
To finish the setup we SSH to the DRAC console and run the following commands:
# The DRAC shell is usually prefixed with something like /admin1-> but
# I will not print it here so you can easily copy/paste this
racadm config -g cfgSerial -o cfgSerialBaudRate 115200
racadm config -g cfgSerial -o cfgSerialCom2RedirEnable 1
racadm config -g cfgSerial -o cfgSerialSshEnable 1
racadm config -g cfgIpmiSol -o cfgIpmiSolEnable 1
racadm config -g cfgIpmiSol -o cfgIpmiSolBaudRate 115200
racadm config -g cfgIpmiLan -o cfgIpmiLanEnable 1
There are settings to limit DRAC network access (HTTPS, SSH, IPMI) to a specific subnet, but I strongly suggest you do not place your DRAC on the internet and protect it with a real firewall. It would be reasonable to enable this bruteforce protection if you wish to do so. The following blocks for 5 minutes after 5 failed attempts:
racadm config -g cfgRacTuning -o cfgRacTuneIpBlkEnable 1
racadm config -g cfgRacTuning -o cfgRacTuneIpBlkFailCount 5
racadm config -g cfgRacTuning -o cfgRacTuneIpBlkFailWindow 60
racadm config -g cfgRacTuning -o cfgRacTuneIpBlkPenaltyTime 300
Now you have remote access to your server without Java. You can access it with one of the following:
ssh:
$ ssh root@1.2.3.4
/admin1-> console com2
ipmi:
$ ipmitool -I lanplus -U root -H 1.2.3.4 sol activate
Both of these will render best if your terminal window is 80x24.
Cisco CIMC
Assuming you've already provisioned an IP address for your Cisco CIMC and it is accessible on the network you can simply ssh into the CIMC and run the following commands:
cisco-cimc# scope sol
cisco-cimc /sol # set baud-rate 115200
cisco-cimc /sol *# set enabled yes
cisco-cimc /sol *# commit
show
cisco-cimc /sol # show
Enabled Baud Rate(bps)
------- ---------------
yes 115200
cisco-cimc# top
cisco-cimc# scope ipmi
cisco-cimc /ipmi # set enabled yes
cisco-cimc /ipmi *# commit
cisco-cimc /ipmi # show
Enabled Encryption Key Privilege Level Limit
------- ---------------------------------------- ---------------------
yes 0000000000000000000000000000000000000000 admin
db02-ipmi /ipmi #
Or for your copy/paste speedrun:
scope sol
set baud-rate 115200
set enabled yes
top
scope ipmi
set enabled yes
commit
Now you can connect to the serial console by one of the following:
ssh:
$ ssh admin@1.2.3.4
cisco-cimc# connect host
ipmi:
$ ipmitool -I lanplus -U admin -H 1.2.3.4 sol activate
The Cisco CIMC also allows you to mount remote media from a fileshare or HTTP/HTTPS URL which is fantastic for troubleshooting. :-)